Technical advice on WannaCry global ransomware attack
CYBER SECURITY software specialists at McAfee have released a technical analysis of the so-called WANNACRY ransomware hack, in an effort to help businesses head off an attack.
McAfee researchers Raj Samani and Christiaan Beek released a blog post with co-author Chris McFarland on May 12 in an effort to get the message out to chief technology officers and ICT staff across Australia.
“Over the course of Friday (May 12) we received multiple reports of organisations across multiple verticals being victim to a ransomware attack,” the McAfee team reported. “Once infected, the encrypted files contain the file extension ‘.WNCRYT’.
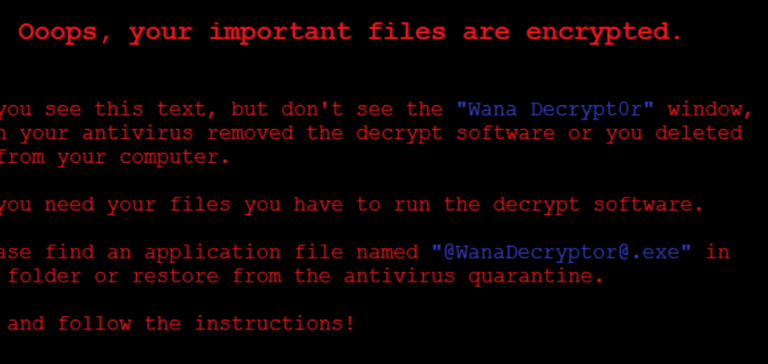
“Victim computers then proceed to display the below message (pictured) with a demand for $300 to decrypt the files.”
McAfee then provided the following technical information:
OBSERVATIONS
Exploit MS17-010:
The malware is using the MS17-010 exploit to distribute itself. This is a SMB vulnerability with remote code execution options – details: https://technet.microsoft.com/en-us/library/security/ms17-010.aspx .
Exploit-code is available on multiple sites including this example: https://github.com/RiskSense-Ops/MS17-010/blob/master/exploits/eternalblue/ms17_010_eternalblue.rb
This exploit is also known as the Equation Group’s ETERNALBLUE exploit, part of the FuzzBunch toolkit released by Shadow Brokers a couple of weeks ago.
With MS17-010, the attacker can use just one exploit to get remote access with system privileges, meaning both steps (Remote Code Execution +Local Privilege Escalation combined) are using just one bug in SMB protocol.
Analyzing the exploit-code in Metasploit, a famous tool used for hacking, the exploit uses ‘KI_USER_SHARED_DATA’ which has a fixed memory address (0xffdff000 on 32 bit Windows) to copy payload to and transfer control to it later.
By remotely gaining control over victim PC with system privileges without any user action, the attacker can spray this malware in local network by having control over one system inside this network (get control over all system which is not fixed and affected by this vulnerability) and that one system will spread the ransomware in this case all over the Windows systems vulnerable and not patched to MS17-010.
Behaviour:
By using command-line commands, the Volume Shadow copies and backups are removed:
Cmd /c vssadmin delete shadows /all /quiet & wmic shadowcopy delete & bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no & wbadmin delete catalog -quiet
File-size of the ransomware is 3.4 MB (3514368 bytes)
Authors called the ransomware “WANNACRY” – string hardcoded in samples.
Ransomware is writing itself into a random character folder in the ‘ProgramData folder with the file name of “tasksche.exe’ or in C:\Windows\ folder with the file-name ‘mssecsvc.exe’ and ‘tasksche.exe’.
Examples:
C:\ProgramData\lygekvkj256\tasksche.exe
C:\ProgramData\pepauehfflzjjtl340\tasksche.exe
C:/ProgramData/utehtftufqpkr106/tasksche.exe
c:\programdata\yeznwdibwunjq522\tasksche.exe
C:/ProgramData/uvlozcijuhd698/tasksche.exe
C:/ProgramData/pjnkzipwuf715/tasksche.exe
C:/ProgramData/qjrtialad472/tasksche.exe
c:\programdata\cpmliyxlejnh908\tasksche.exe
Ransomware is granting full access to all files by using the command:
Icacls . /grant Everyone:F /T /C /Q
Using a batch script for operations:
176641494574290.bat
Content of Batch-file (fefe6b30d0819f1a1775e14730a10e0e)
echo off
echo SET ow = WScript.CreateObject(“WScript.Shell”)> m.vbs
echo SET om = ow.CreateShortcut(“C:\
WanaDecryptor
.exe.lnk”)>> m.vbs
echo om.TargetPath = “C:\
WanaDecryptor
.exe”>> m.vbs
echo om.Save>> m.vbs
cscript.exe //nologo m.vbs
del m.vbs
del /a %0
Content of ‘M.vbs’
SET ow = WScript.CreateObject(“WScript.Shell”)
SET om = ow.CreateShortcut(“C:\
WanaDecryptor
.exe.lnk”)
om.TargetPath = “C:\
WanaDecryptor
om.Save
Indicators of compromise
Hashes:
dff26a9a44baa3ce109b8df41ae0a301d9e4a28ad7bd7721bbb7ccd137bfd696
201f42080e1c989774d05d5b127a8cd4b4781f1956b78df7c01112436c89b2c9
ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa
c365ddaa345cfcaff3d629505572a484cff5221933d68e4a52130b8bb7badaf9
09a46b3e1be080745a6d8d88d6b5bd351b1c7586ae0dc94d0c238ee36421cafa
b9c5d4339809e0ad9a00d4d3dd26fdf44a32819a54abf846bb9b560d81391c25
aae9536875784fe6e55357900519f97fee0a56d6780860779a36f06765243d56
21ed253b796f63b9e95b4e426a82303dfac5bf8062bfe669995bde2208b360fd
2372862afaa8e8720bc46f93cb27a9b12646a7cbc952cc732b8f5df7aebb2450
24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c
f8812f1deb8001f3b7672b6fc85640ecb123bc2304b563728e6235ccbe782d85
4a468603fdcb7a2eb5770705898cf9ef37aade532a7964642ecd705a74794b79
4b76e54de0243274f97430b26624c44694fbde3289ed81a160e0754ab9f56f32
9cc32c94ce7dc6e48f86704625b6cdc0fda0d2cd7ad769e4d0bb1776903e5a13
78e3f87f31688355c0f398317b2d87d803bd87ee3656c5a7c80f0561ec8606df
be22645c61949ad6a077373a7d6cd85e3fae44315632f161adc4c99d5a8e6844
5d26835be2cf4f08f2beeff301c06d05035d0a9ec3afacc71dff22813595c0b9
76a3666ce9119295104bb69ee7af3f2845d23f40ba48ace7987f79b06312bbdf
fc626fe1e0f4d77b34851a8c60cdd11172472da3b9325bfe288ac8342f6c710a
eeb9cd6a1c4b3949b2ff3134a77d6736b35977f951b9c7c911483b5caeb1c1fb
043e0d0d8b8cda56851f5b853f244f677bd1fd50f869075ef7ba1110771f70c2
57c12d8573d2f3883a8a0ba14e3eec02ac1c61dee6b675b6c0d16e221c3777f4
ca29de1dc8817868c93e54b09f557fe14e40083c0955294df5bd91f52ba469c8
f7c7b5e4b051ea5bd0017803f40af13bed224c4b0fd60b890b6784df5bd63494
3e6de9e2baacf930949647c399818e7a2caea2626df6a468407854aaa515eed9
9b60c622546dc45cca64df935b71c26dcf4886d6fa811944dbc4e23db9335640
5ad4efd90dcde01d26cc6f32f7ce3ce0b4d4951d4b94a19aa097341aff2acaec
24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c
12d67c587e114d8dde56324741a8f04fb50cc3160653769b8015bc5aec64d20b
85ce324b8f78021ecfc9b811c748f19b82e61bb093ff64f2eab457f9ef19b186
3f3a9dde96ec4107f67b0559b4e95f5f1bca1ec6cb204bfe5fea0230845e8301
IP-Addresses:
- 197.231.221.221:9001
- 128.31.0.39:9191
- 149.202.160.69:9001
- 46.101.166.19:9090
- 91.121.65.179:9001
- 2.3.69.209:9001
- 146.0.32.144:9001
- 50.7.161.218:9001
- 217.79.179.177:9001
- 213.61.66.116:9003
- 212.47.232.237:9001
- 81.30.158.223:9001
- 79.172.193.32:443
- 38.229.72.16:443
Domains:
- iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com (sinkholed)
- Rphjmrpwmfv6v2e[dot]onion
- Gx7ekbenv2riucmf[dot]onion
- 57g7spgrzlojinas[dot]onion
- xxlvbrloxvriy2c5[dot]onion
- 76jdd2ir2embyv47[dot]onion
- cwwnhwhlz52maqm7[dot]onion
File Names:
- @Please_Read_Me@.txt
- @WanaDecryptor@.exe
- @
This email address is being protected from spambots. You need JavaScript enabled to view it. - Please Read Me!.txt (Older variant)
- C:\WINDOWS\tasksche.exe
- C:\WINDOWS\qeriuwjhrf
- 131181494299235.bat
- 176641494574290.bat
- 217201494590800.bat
- [0-9]{15}.bat #regex
- !WannaDecryptor!.exe.lnk
- 00000000.pky
- 00000000.eky
- 00000000.res
- C:\WINDOWS\system32\taskdl.exe
Bitcoin Wallets
- 115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
- 13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94
- 12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw
Here is a snort rule submitted to Sans from Marco Novak:
alert tcp $HOME_NET 445 -> any any (msg:”ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Response”; flow:from_server,established; content:”|00 00 00 31 ff|SMB|2b 00 00 00 00 98 07 c0|”; depth:16; fast_pattern; content:”|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|”; distance:0; flowbits:isset,ETPRO.ETERNALBLUE; classtype:trojan-activity; sid:2024218; rev:2;)
And other SNORT rules from Emerging Threats:
(http://docs.emergingthreats.net/bin/view/Main/2024218)
alert smb any any -> $HOME_NET any (msg:”ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Request (set)”; flow:to_server,established; content:”|00 00 00 31 ff|SMB|2b 00 00 00 00 18 07 c0|”; depth:16; fast_pattern; content:”|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|”; distance:0; flowbits:set,ETPRO.ETERNALBLUE; flowbits:noalert; classtype:trojan-activity; sid:2024220; rev:1;)
alert smb $HOME_NET any -> any any (msg:”ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Response”; flow:from_server,established; content:”|00 00 00 31 ff|SMB|2b 00 00 00 00 98 07 c0|”; depth:16; fast_pattern; content:”|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|”; distance:0; flowbits:isset,ETPRO.ETERNALBLUE; classtype:trojan-activity; sid:2024218; rev:1;)
Yara:
rule wannacry_1 : ransom
{
meta:
author = “Joshua Cannell”
description = “WannaCry Ransomware strings”
weight = 100
date = “2017-05-12”
Strings:
$s1 = “Ooops, your files have been encrypted!” wide ascii nocase
$s2 = “Wanna Decryptor” wide ascii nocase
$s3 = “.wcry” wide ascii nocase
$s4 = “WANNACRY” wide ascii nocase
$s5 = “WANACRY!” wide ascii nocase
$s7 = “icacls . /grant Everyone:F /T /C /Q” wide ascii nocase
Condition:
any of them
}
rule wannacry_2{
meta:
author = “Harold Ogden”
description = “WannaCry Ransomware Strings”
date = “2017-05-12”
weight = 100
strings:
$string1 = “msg/m_bulgarian.wnry”
$string2 = “msg/m_chinese (simplified).wnry”
$string3 = “msg/m_chinese (traditional).wnry”
$string4 = “msg/m_croatian.wnry”
$string5 = “msg/m_czech.wnry”
$string6 = “msg/m_danish.wnry”
$string7 = “msg/m_dutch.wnry”
$string8 = “msg/m_english.wnry”
$string9 = “msg/m_filipino.wnry”
$string10 = “msg/m_finnish.wnry”
$string11 = “msg/m_french.wnry”
$string12 = “msg/m_german.wnry”
$string13 = “msg/m_greek.wnry”
$string14 = “msg/m_indonesian.wnry”
$string15 = “msg/m_italian.wnry”
$string16 = “msg/m_japanese.wnry”
$string17 = “msg/m_korean.wnry”
$string18 = “msg/m_latvian.wnry”
$string19 = “msg/m_norwegian.wnry”
$string20 = “msg/m_polish.wnry”
$string21 = “msg/m_portuguese.wnry”
$string22 = “msg/m_romanian.wnry”
$string23 = “msg/m_russian.wnry”
$string24 = “msg/m_slovak.wnry”
$string25 = “msg/m_spanish.wnry”
$string26 = “msg/m_swedish.wnry”
$string27 = “msg/m_turkish.wnry”
$string28 = “msg/m_vietnamese.wnry”
condition:
any of ($string*)
}
https://securingtomorrow.mcafee.com
ends

 How to resolve AdBlock issue?
How to resolve AdBlock issue?